Ransomware is one of the critical cyber-attacks experienced by small and medium-sized businesses (SMBs). An earlier IBM study suggests that 50% of companies don’t even factor security as part of their mobile app development budget.
With 40% of them not reviewing the application code, and investigating the possible security gaps. As a result, nearly 1,000 million users and business data are exposed to cyber-attacks.
Organizations develop android applications at breakneck speed to meet business needs. And, yet they fail to consider Android app security as part of their app development focus. Our article aims to provide a holistic android app security checklist. It lists down the best practices to protect applications from malware attacks.

Application Security For The Android Platform
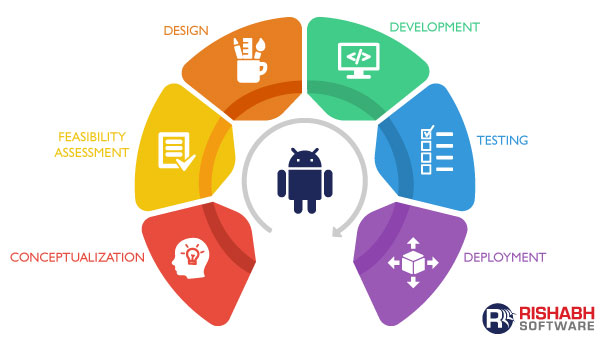
Android best practices for security & privacy helps define the right approach throughout the application lifecycle.
-
- Secure The Server
Hackers often try to attack the server and its API. It means you must secure the server and API to install controls and prevent attacks. Adding a new Web application firewall or conducting code reviews will help overcome this challenge. - Data Encryption
Mobile app security involves securing all kinds of stored data on the mobile device. It includes the source code as well as the data transmitted between the application and the back-end server. The execution of certificate pinning helps affirm the backend Web service certificate for the application. High-level data encryption is one of the best android mobile app security practices. It protects the valuable data from hackers. - Code Obfuscation
Protect the source code by making it unintelligible for both humans and decompiler. All this, while preserving its entire operations during the compilation. The purpose of the obfuscation process is to give an impenetrable code. It promotes the confidentiality of all intellectual properties against reverse engineering. Therefore, it gets listed among android application security best practices. - High-Level User Authentication
Multi-factor authentication, a disconnection system, and proper session management help protect sensitive information. It is also essential to set up advanced authorization with the support of tools such as OAuth 2.0 or JSON web tokens for added security of Android apps. The secure and integrated access gateway ensures that only compliant devices and authorized applications can access corporate resources.
- Secure The Server
Is Your Android Application Secure?
Our experienced Android development team will help you build a robust and secure mobile app
- Protecting Transit Data
Proactive defenses, such as advanced jailbreak detection and status-based access control, devices declared non-compliant cannot access corporate data. In case of theft or loss of a device, you can delete applications and business data, so that they do not fall into the wrong hands. Selective data erasure allows users or the IT department to wipe enterprise data stored on a device remotely. - Regular Updation And Testing
Hackers detect vulnerabilities in software and exploit, while developers repair the breach, which causes hackers to discover another weakness. Although Google cannot avoid the development of these vulnerabilities, it effectively updates the Android OS to counter the detected problems. However, these measures will not be useful if the software is not up-to-date. Penetration testing is another method for server-side checks. - Code Tamper Detection
The android application security checklist also includes deploying anti-tamper techniques such as anti-virus, signature verification mechanisms, activity logs to keep a check on vulnerable or infected libraries added in your application’s source code. - Client Side Data Storage
Data stored in mobile devices is exposed in case of theft or loss of equipment. Also, a mobile device is not necessarily secure, since many users unlock (jailbreak or root) their device to access additional features and software. This process removes a significant security layer. Hence, sensitive data must be stored on the server side. - Principle Of Least Privilege
Limiting access to the application data is one of the critical android application security best practices. It offers both system security and stability. Further, it protects the data from faults and malicious behavior. You can do this in the settings of the Android device, but take into account that this might hinder application functioning. - Security And Confidentiality
The use of encryption key of at least 128 bits is recommended as part of the Advanced Encryption Standard (AES). The purpose of pinning certificate, along with the use of a hash further helps to strengthen the security. It comprises of returning the entire request in the form of a hashed string with a secret key. The server compares this string with the request it receives to verify any modifications or changes in the meantime.
Conclusion:
Most of the security breaches are a result of shortcomings during the development and configuration of Android applications. For this, external audits are possible, and recommendations exist:
- Use the architecture standards of the OWASP
- Integrate security teams upstream, do a risk analysis and set up a mobile security management approach on the project
- Identify the prerequisites concerning personal data protection
- Identify the relevant security standards and regulations
- Plan and monitor the deployment of antivirus and firewalls on the phone that control the illegal installation of code on the device
- For the most critical applications in sensitive locations, consider deploying a biometric authentication
- Customize the factory default settings
- Perform regular code reviews and in-depth audits
- Train your developers or carefully select your Android application development service partner