Application security is a critical aspect of any cloud ecosystem. It enables businesses to become more agile while eliminating security risks. Businesses today manage an isolated virtual private environment over a public cloud infrastructure. While it is a business decision whether to manage cloud infrastructure offered by public cloud providers or to maintain it with an in-house IT Team or have a hybrid one, securing the application delivery is always of primary concern. That is where cloud application security comes into play. It helps protect cloud-based apps, data, and infrastructure with the right combination of well-defined models, processes, controls, and policies.
This blog explores cloud application security importance, common threats, solutions, and how we can lend a helping hand by adopting cloud application security best practices. We will also walk you through a Cloud application security checklist to ensure you take the right steps toward a secured cloud-first organization. So, let’s dive in.
What Is Cloud Application Security?
Cloud Application Security is a process of safeguarding applications across the entire cloud environment from potential threats, attacks, and vulnerabilities. Cloud application security involves a comprehensive approach to deploying technology, processes, and policies to ensure that the security of cloud-based applications is not compromised.
Why is Cloud App Security Important?
At present, businesses are using a variety of solutions in the multi-cloud environment to enable productivity. But the assortment of unmonitored and unmanaged apps & cloud services can often expose cloud-based applications to a wide range of attacks. Whether using SaaS, IaaS, PaaS, or a mix of these architectures, we all use applications daily, and attackers seek to exploit those applications to achieve their goals.
Cloud app security is exclusively designed to protect your organization’s sensitive data from vulnerabilities such as data breaches, cyber threats, and data loss.
Cloud Application Security Issues and Solutions
Cloud security applications are exposed to various risks and vulnerabilities. We dive deep into the most common cloud application security issues along with their solutions.

Cloud Misconfigurations
Threat:
Misconfigurations of cloud resources are the most common cloud vulnerability. Configuration errors, oversights, or intentional misconfiguration of cloud environments, applications, or security settings by someone inside the organization can put cloud-based applications at risk.
Solution:
Deploy policy-based automation at every stage of the development life cycle, from IaC (infrastructure as a code) to CI/CD to runtime. Regularly audit cloud environments and choose cloud-based automation to monitor and enforce security. Well-organized cloud governance is also crucial to a robust environment.
Multi-Tenant Vulnerabilities
Threat:
Multi-tenant offers cost efficiency & scalability, and the shared tenancy brings security and privacy concerns. It results in
- Lack of visibility into accounts
- Overallocation and inconsistent assignment of privileges
- Poor data security management
Solution:
Implement efficient isolation to improve your system encryption protocols and access controls. Utilize data loss prevention solutions to monitor, analyze, notify, and block suspicious and unauthorized sessions. Partnering with an experienced SaaS application development company ensures that multi-tenant platforms are designed with the right isolation, encryption, and access controls to minimize such risks.
Denial of Service (Dos) Attacks
Threat:
A DoS attack aims to disrupt cloud application performance, resulting in downtime, loss of revenue, and reputation.
Solution:
Implementing proactive measures such as creating VLANs, setting up firewalls, IP blocking, and enforcing load balancing to distribute traffic across multiple servers can help detect early signs of a DoS attack.
Insecure APIs
Threat:
Insecure REST APIs can allow attackers direct access to sensitive data on the backend system. There are chances of exposing important data and risk of unauthorized access.
Solution:
Choose standard API frameworks such as OCCI and CIMI for strict security controls. Using a Cloud Native Application Protection Platform, implement end-to-end security to ensure vulnerability management, threat detection, and response capabilities.
Malware File Upload Security
Threat:
Hackers can upload malicious files that could compromise your system’s security.
Solution:
Implement OWASP- Open Worldwide Application Security Project to prevent file upload attacks. Here you also need to ensure that you only allow specific file types and verify file types against the whitelist. Use a captcha to prevent uploads by bots and reconstruct CDR to remove any possible threats embedded in documents.
Cloud Application Security Best Practices
Here are 6 cloud application best practices that you can implement for effective cloud security.
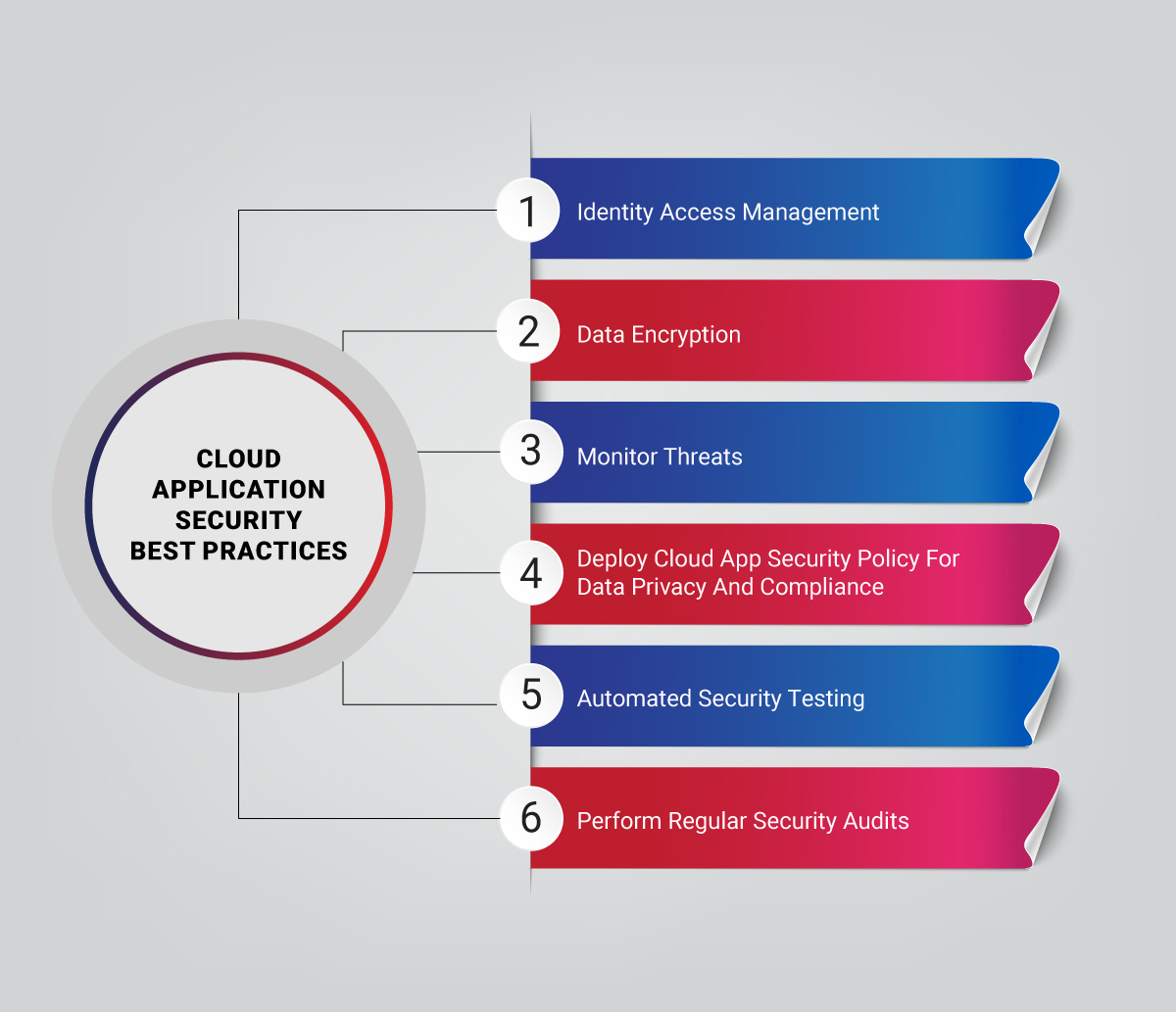
Identity Access Management
Integrating your Identity Access Management (IAM) approach with the overall cloud security strategy is essential to leverage full benefits. Adopting a zero-trust security approach, adopting Multi-Factor Authentication (MFA), Single Sign-On (SSO) tools ensures that every user is authenticated and can access only authorized applications and data.
Data Encryption
Encryption helps to protect data and optimize cloud application performance. There are three types of data encryption you must focus on:
- Data In-Transit Encryption: It involves encrypting data between internal or external sources. It aims to secure data while in transit between cloud systems or end-users so that third parties do not intercept it.
- Data At Rest Encryption: This practice ensures that unauthorized users cannot interpret data while it is stored in the cloud. It consists of creating multiple layers of encryption at the hardware, file, and database levels to protect sensitive application data from data breaches.
- Data-in-use Encryption: Encryption-in-use aims to secure data that is being processed presently. Implementing role-based access controls, IAM, and MFA are good practices to limit access and keep data safe.
Monitor Threats
It is critical to constantly monitor threats in real-time to detect any unusual behavior and respond quickly. As cyberattacks and data breach landscape become more sophisticated, it becomes important to leverage threat intelligence data to stay ahead of attackers with malicious intent. Adopting this best practice allows your cloud security team to proactively detect the threats rapidly, take immediate actions, and minimize the damage of the cyberattack.
Deploy Cloud App Security Policy for Data Privacy and Compliance
A comprehensive cloud application security policy is critical to safeguard cloud apps and end users. The cloud security policy defines security principles, rules, procedures, and governance for all cloud services and applications. From outlining the organization’s requirements for cloud security to enforcing access controls and data encryption, these must be implemented across the organization.
Automated Security Testing
A critical best practice of cloud application security is embedding DevSecOps into each stage of the application development process. It includes scanning the code, open-source libraries, container images, and infrastructure configurations for vulnerabilities and threats.
Following this best practice not only streamlines the development process and improves efficiency but also ensures that each application is secured before using them for cloud deployment. Further, integrating Shift Left testing with DevSecOps allows you to introduce testing right from the early stages of app development. Testing early and often allows your team to scan the application quickly and accurately for any threats or malicious attacks.
Perform Regular Security Audits
According to a study by World Economic Forum[1], human error is the main cause of 95% of cyberattack data breaches. So, performing weekly, monthly, or quarterly cloud security audits is advisable.
These security audits ensure that cloud applications and data are safe from unauthorized access and can prevent data breaches. Cloud security audit includes inspection of security controls put in place by the organization to protect data and cloud application security. The audit usually has a cloud application security checklist in place to ensure that the expected security posture of the organization is as per the mark.
Cloud Application Security Checklist
Here is a top 10-point checklist to deploy zero trust security and mitigate issues for your cloud applications.
| Password policies |
|
| Multi-factor authentication |
|
| Access & permissions |
|
| External sharing standards |
|
| Vulnerability assessment |
|
| Business continuity |
|
| Data loss prevention |
|
| Message encryption & mobile management |
|
| Network traffic & access log |
|
| Service Level Agreement (SLA) standards |
|
Working with an experienced cloud consulting firm, like Rishabh Software, can help you curate a custom cloud application security checklist that suits your organization’s security requirements.
How Rishabh Software’s Cloud-based Application Security Service Delivers Value
In the digital era of collaborative cloud environments, our cloud experts can help you safeguard applications, data, and infrastructure to secure your cloud environments. Leverage our expertise in custom cloud applications to increase the security of your cloud application from start to finish. It is with
- Assessment – Evaluating the application architecture and security controls to identify potential risks
- Planning – Mapping your cloud app security roadmap, including strategies, capabilities, and activities
- Implementation – Building & deploying custom cloud applications with baseline security controls
- Awareness – Enabling teams to identify security risks with evolving solutions & regulatory requirements through a shared responsibility model.
As your one-stop solution for full-cycle custom cloud application development services, we can help you develop apps from scratch ensuring all the security criteria. Our skilled team of cloud engineers is well-versed in simplifying the complex cloud application development landscape by implementing modern technologies.
Conclusion
As more and more businesses adopt modern cloud-based app development, there will likely be a further increase in the threats and an immediate need to embed best practices in cloud application security.
As a result, businesses must invest in advanced cloud application security to safeguard data and infrastructure against threats and data breaches. That’s why it’s critical to implement robust Cloud Application security best practices to ensure data confidentiality, integrity, and availability. It helps protect your organization’s reputation and customer trust.
FAQ
Q: Why Cloud Application Security Is Need of the Hour?
A: With the rush to the cloud over the past few years and the rise in data breaches and cyberattacks, the C-suite demands greater visibility into the risk contributions of cloud applications. Organizations fast recognize the need for cloud application security across the complete lifecycle of an application – development, testing, deployment, to maintenance.
Cloud-based applications are susceptible to unauthorized access, data breaches, and cyberattacks. Cloud applications often integrate with diverse services, APIs, and third-party components, heightening the attack surface. Ensuring robust identity management, encryption, access controls, and continuous monitoring is essential to protect sensitive data, maintain compliance, and combat evolving threats in the ever-changing cloud landscape. Proactively discovering vulnerable applications allows DevOps teams to stay ahead of threats while maintaining release velocity and ensuring efficient use of security budgets.
Q: What Are the Types of Cloud Application Security?
A: There are main three types of cloud application security frameworks:
- CASB – Cloud Access Security Broker: From authentication and credential mapping to encryption and malware detection, CASBs help maintain regulatory compliance and provide visibility into cloud application security.
- CSPM – Cloud Security Posture Management: CSPM helps detect misconfiguration issues and compliance risks that could lead to sensitive data breaches or compliance violations.
- CWPP – Cloud Workload Protection Platform: CWPPs protect workloads of all types in any location, offering protection for cloud application security across multiple providers.
Q: What Is the Shared Responsibility Model?
A: In cloud application security, the responsibilities for security and compliance are shared between the cloud provider and the customer. The cloud service provider like AWS, Microsoft Azure, or Google is responsible for safeguarding the infrastructure, whereas the customer is accountable for securing the cloud application, data, and access. The shared responsibilities also vary based on the cloud service model – SaaS, PaaS, or IaaS.
Footnotes:
1. https://www3.weforum.org/docs/WEF_The_Global_Risks_Report_2022.pdf










 30 Min
30 Min


