SaaS apps power your business. But in 2025, they’re also powering a new wave of threats.
Just ask Oracle.
In early 2025, attackers exploited a legacy Oracle cloud server—still connected to live identity infrastructure, and leaked federated SSO credentials [1] tied to active systems. Oracle called it old news. Their customers didn’t.
Because incidents like this don’t stay inside IT.
They ripple outward—shaking customer trust, triggering board-level fallout, and risking revenue at scale.
Here’s the kicker. That same identity layer powers tools your team uses daily—ChatGPT Enterprise, Microsoft Copilot, Notion AI. Once compromised, attackers can view sensitive AI interactions without ever touching the AI itself.
The breach isn’t coming through the front door—it’s walking in with a valid login.
Shadow AI tools, dormant admin accounts, old OAuth tokens, and sprawling federated identities as are your current attack surface.
That’s why SaaS security best practices in 2025 aren’t just a checklist—they’re a lifeline.
So, secure your SaaS stack from the inside out—before a misconfigured identity costs you millions. Let’s unpack how to fix what’s quietly breaking your SaaS stack.
The SaaS Security Challenges You Can’t Afford to Ignore in 2025
The problem isn’t your firewalls or weak passwords anymore. What’s quietly eroding your security is the invisible layer: visibility, control, and accountability.
Freemium AI tools, unapproved SaaS extensions, over-permissioned user roles are not just risks; they are being exploited in real time.
If you don’t know what apps are running, who has access, or where your data lives, you’re not just exposed — you’re behind.
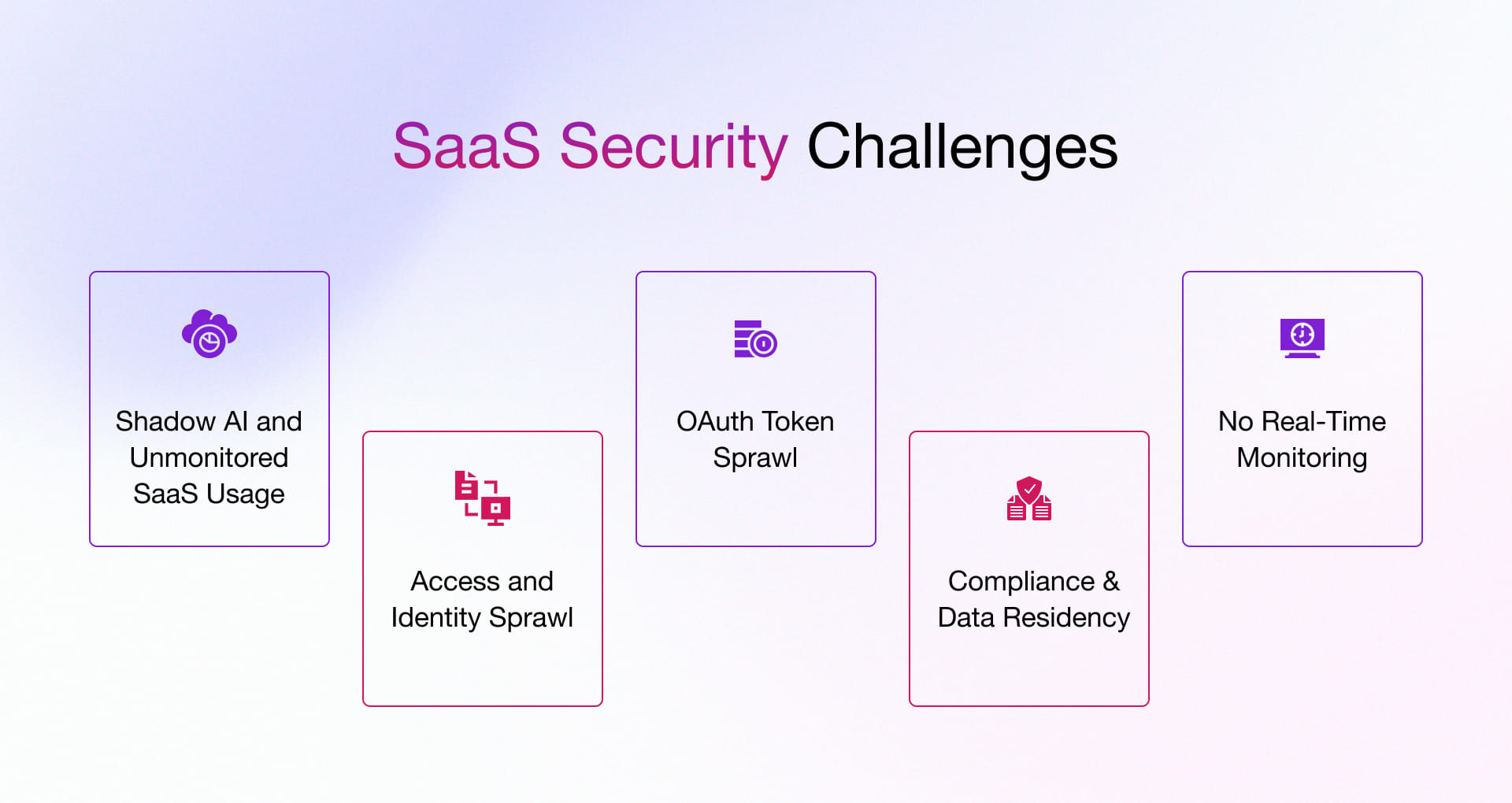
Challenge #1: Shadow AI and Unmonitored SaaS Usage
In 2025, your biggest threat isn’t malware, it’s your own employees- integrating AI tools you’ve never vetted
Browser-based copilots, AI writing assistants, and analytics extensions now enter your environment without security review, often storing sensitive data: customer PII, code, financials, in systems outside your control.
These tools often bypass procurement, lack encryption standards, and thrive on ingesting the exact data you’re trying to protect.
Even Microsoft wasn’t immune. In 2024, its AI research team accidentally exposed 38TB of internal data[2], including Teams messages and credentials, due to misconfigured AI storage.
The business risk? Massive. You’re looking at potential compliance violations, loss of IP, and trust erosion, all without a single alert from your current stack.
To avoid multiplying it, deploy a SaaS Security Posture Management (SSPM) with shadow AI detection, browser-level telemetry, and policy enforcement. Block unvetted tools. Monitor OAuth scopes.
Challenge #2: Access and Identity Sprawl
Here’s the uncomfortable truth: in most enterprises, users have more access than they need – and attackers know it.
Think about all the SaaS apps you’ve approved. Each one adds roles, tokens, and admin rights, but no one audits them regularly.
Over time, dormant superusers remain active, OAuth tokens never expire, and permissions pile up – quietly.
On the business front, one compromised account derails compliance, destroys trust, and triggers real financial consequences.
You won’t get a warning. So, enforce the least privilege, run access audits, and centralize identity governance across your SaaS stack starting today.
Challenge #3: OAuth Token Sprawl
OAuth was supposed to simplify access. In 2025, it’s become one of the most overlooked risks in SaaS environments.
Every time someone connects a third-party app to your systems: a calendar plugin, an AI productivity tool, or a CRM extension, your system issues an OAuth token. These tokens often carry broad, persistent permissions. They don’t expire quickly. And most companies don’t track them.
Over time, these credentials pile up; tied to inactive users or forgotten apps. Since they operate outside your identity provider, they stay active even after employee offboarding or password resets.
This is how modern breaches unfold: quietly, without alerts.
What’s at stake? Persistent exposure. Loss of control over who, or what, is accessing your core SaaS tools. And because OAuth sprawl rarely shows up in traditional audits, most organizations don’t even know they’re vulnerable.
Fix it with visibility. Map and manage token lifecycles across your SaaS stack.
Planning to build a SaaS product from the ground up? Explore our SaaS product development guide for strategies that blend scalability, security, and speed led.
Challenge #4: Compliance and Data Residency
Thanks to Generative AI, compliance is a moving target, unlike the old, checkbox.
GenAI tools now shift how and where your data moves. Your sensitive inputs are processed across global data centers, logged by third-party AI engines, and stored without clear visibility into residency or retention policies.
And regulators are catching up fast. The EU’s AI Act enforces transparency around data usage in AI models. India’s DPDP Act introduces strict rules around consent and cross-border transfers. Similar laws in China, Brazil, and others are expanding how enterprise data is governed.
You can’t prove compliance if you don’t know where your data flows. This liability could cost you fines, contract risk, and customer churn. A single AI tool processing data outside approved geographies could risk your compliance posture.
What would help?
Centralized visibility into SaaS data flows, automated checks for geo-boundary violations, and strong vendor governance, especially for AI-powered tools operating across borders.
Challenge #5: No Real-Time Monitoring
Most breaches aren’t discovered in real time. They’re found weeks later, after the damage is done.
Today’s attackers don’t break in. They blend in using legitimate credentials and moving through systems slowly. And without real-time behavioral analytics, there’s no way to tell if a user action is routine or a red flag.
Now, there’s a new threat vector: ransomware-in-the-browser. These attacks don’t hit your endpoint security tools. They target SaaS apps directly. And without anomaly detection, they go unnoticed until systems are encrypted or data is exfiltrated.
A SquareX report[3] warns this trend is becoming a serious threat. And without real-time monitoring, attackers can infiltrate SaaS applications and encrypt critical data before security teams even become aware of the issue.
In 2025, static logs and weekly audit reviews won’t cut it. You need continuous monitoring that understands normal user behavior and flags what isn’t.
What’s at stake? Missed breach windows. Reputational loss. And operational downtime when your SaaS tools, the ones your teams rely on daily, go dark without warning.
Go for smarter monitoring, tools that learn patterns, while flagging unusual activity, and alerting your teams in real time.
Proven SaaS Security Best Practices
By now, you’re already aware of where the cracks are: shadow AI, token sprawl, identity chaos, and blind spots you can’t afford. The question now is how to secure SaaS applications before those cracks turn into full-blown breaches.
In 2025, SaaS security is less about reacting and more about operationalizing the right controls before attackers get a head start. Let’s get into what actually works.

Make SaaS Visibility a Continuous Function
If you can’t see it in real time, you can’t secure it. Period.
SaaS visibility isn’t about building static app inventories — it’s about continuously knowing what’s running, who’s using it, what data it touches, and whether it belongs. As part of SaaS application security best practices, this means going beyond surface-level discovery.
Integrate an SSPM platform with your identity infrastructure (e.g., Google Workspace, Okta, Azure AD) and layer it with browser and email telemetry. This helps uncover unsanctioned tools, risky plugins, and AI extensions operating outside policy.
SSPM platforms should do more than observe — they must enforce:
- Auto-quarantine apps requesting high-risk OAuth scopes
- Block tools that fail vendor security checks
- Auto-expire unused apps after 30 days
- Route risk signals to your SIEM, SOAR, or Slack channels
- Track unmanaged browser plugins
Move from observability to enforceability. Because if your tools can’t act in real time, they aren’t securing anything.
Leverage AI/ML for Enhanced Security
Manual detection can’t keep pace with modern SaaS environments. You need AI that doesn’t just alert: it learns, adapts, and responds in real time.
At the core of modern SaaS security principles is intelligent automation, starting with behavior-based detection systems like User and Entity Behavior Analytics (UEBA) to baseline normal activity across users, systems, and integrations. Then, layer machine learning models that score risks dynamically based on evolving patterns, not static rules.
Integrate these insights with SOAR workflows to automate action: suspend sessions, revoke access, or trigger additional authentication without delay.
AI-powered security must also be explainable. Every decision, especially around insider threats or credential abuse, should be understandable to auditors, security teams, and leadership.
Secure Data in Transit and at Rest
Most SaaS platforms claim to offer “end-to-end encryption,” but it often ends at the front door. Once inside, data remains exposed to internal misuse, excessive access, and unauthorized duplication.
The solution is to design your security architecture assuming a breach.
Encrypt data not just in transit and at rest, but also while in use. Apply field-level encryption for sensitive information, and limit decryption to only the services that need it. Use Bring Your Own Key (BYOK) or Hold Your Own Key (HYOK) models to ensure customers retain control of their data access.
Tokenize personally identifiable information (PII) flowing through APIs so it never ends up in logs or analytics. Integrate Data Security Posture Management (DSPM) tools that can identify context-driven risks, such as credit card details in debug files.
In 2023 MOVEit data breach[4], attackers exploited a vulnerability to access sensitive files from over 2,700 organizations. The issue wasn’t a lack of encryption; it was that data was accessible once inside the system, without additional safeguards.
The takeaway: Encryption alone won’t ensure SaaS data security. Control how it’s accessed and processed to limit the damage.
Conduct Regular Security Assessments
Annual audits aren’t enough. Modern SaaS environments evolve too quickly for static reviews to keep up.
Use dynamic application security testing (DAST), cloud-native pentesting tools, and automated configuration drift checks as part of your CI/CD pipeline. Tools like Astra Pentest, Detectify, and Prowler help scan continuously without disrupting development. Red teaming should target production environments to reflect real-world threats.
Establish a structured process:
- Set assessment frequency based on risk exposure
- Align remediation with sprint cycles
- Prioritize issues using threat intelligence
- Log outcomes into your SSPM or SIEM for visibility and accountability
Today, resilience depends on how fast you respond. Assess continuously to detect and resolve issues before they become incidents.
Monitor for Suspicious Activity
Traditional logging is reactive. By the time a SIEM alert fires, the damage may already be done. Modern SaaS security requires behavioral monitoring that can detect intent, not just events.
In December 2024, attackers used stolen credentials to publish a malicious version of the Cyberhaven Chrome extension [5] It stayed live for 31 hours, exfiltrating user data from over 400,000 users. Real-time monitoring could have detected the anomaly before the breach escalated.
So, start with User and Entity Behavior Analytics (UEBA) to track anomalies across logins, location shifts, permission escalations, and unusual data flows. Tools like Exabeam, Splunk, and Sekoia.io help establish baselines and adjust dynamically using machine learning.
Make detection workflows actionable:
- Map high-risk behaviors to real-time policies
- Route anomalies to SOAR systems for investigation or access revocation
- Enrich alerts with user context like role, device, and location
- Focus alerts only on suspicious behavior that needs action
Develop Strong Vendor Security Assessment Processes
In a SaaS environment built on integrations, vendors often become your most exposed entry point. One poorly vetted connection can compromise critical data.
Replace checkbox-based reviews with continuous, risk-driven assessments. Use platforms like Whistic, Vanta, or SecurityScorecard to automate due diligence, track vendor risk, and enable real-time monitoring.
Make your process actionable:
- Block OAuth scopes from vendors that don’t meet security requirements
- Auto-expire access for vendors lacking up-to-date compliance documentation
- Route abnormal vendor activity to SIEM or access control workflows
- Include security clauses in contracts to cover breach notifications, audit rights, and incident handling
Also worth keeping in check: employee awareness, SaaS-specific backups, and incident response protocols. They’re not silver bullets, but they’re core to the best practices for securing SaaS applications—limiting the impact radius when things go wrong.
Make the Next Move Now
Securing your SaaS environment isn’t just about tools. It’s about having the right partner. At Rishabh Software, we don’t just build SaaS products. We engineer them on a secure-by-design SaaS architecture, so you’re not patching vulnerabilities after launch but preventing them from day one.
Our end-to-end SaaS development services integrate cloud-native security, identity governance, data protection, and real-time threat detection from day one. With deep expertise in AI/ML, compliance frameworks, and zero-trust architecture, we help enterprises design secure, scalable SaaS solutions built to withstand modern attack surfaces.
And while these advanced controls matter, don’t overlook the basics. Consistent employee training, reliable SaaS backups, and a tested incident response plan still play a critical role in limiting the impact when things go wrong.
If you’re looking to develop with resilience instead of reactively fixing what breaks, let’s talk.
Frequently Asked Questions
Q – What are the benefits of SaaS Security?
A – SaaS security helps protect your business from data breaches, compliance violations, and insider threats. It ensures that only authorized personnel can access critical data while blocking unauthorized users. A robust security framework maintains customer trust, prevents downtime, and minimizes financial losses caused by cyberattacks. With the proper security measures in place, you can scale safely without worrying about gaps that attackers might exploit.
Q – How often should enterprises conduct SaaS security audits?
A – At a minimum, enterprises should conduct a comprehensive security audit at least every six months. However, this alone is not enough. Continuous monitoring and monthly mini-audits are crucial for identifying misconfigurations early. Real-time threat detection tools should run 24/7 to identify anomalies before they escalate.
Q – What key security questions should enterprises ask SaaS vendors before onboarding?
A – Here are the questions that you need to ask SaaS vendors—because every integration, permission, and API call is a SaaS security consideration you can’t afford to overlook.
- How do you protect customer data?
- Are you compliant with security regulations?
- What authentication and access controls do you provide?
- How do you detect and respond to security incidents?
- How secure are your APIs?
- How do you manage third-party security risks?
- What happens to our data after the contract ends?
- Do you offer visibility into security logs?
- What DDoS protection measures do you have in place?
- How do you ensure business continuity?
A secure SaaS vendor prioritizes transparency, compliance, and proactive security. If they can’t confidently answer these, it’s a red flag.
Q – How do AI-driven threats impact SaaS security, and how can enterprises defend against them?
A – AI enables faster, difficult-to-detect cyberattacks. Hackers use AI to automate phishing attacks, bypass authentication, and exploit vulnerabilities. Deepfake scams and AI-generated malware increase the risk. To defend against AI-driven threats:
- Use AI-powered threat detection to spot unusual SaaS activity.
- Automate response with AI-driven security tools.
- Enforce Zero Trust to limit unauthorized access.
- Block AI-generated phishing using machine learning.
- Monitor APIs to prevent automated attacks.
- Train employees to spot AI-driven scams and deepfakes.
AI-powered threats need AI-powered security. Enterprises must adapt fast.
Footnotes:
- https://www.bleepingcomputer.com/news/security/oracle-privately-confirms-cloud-breach-to-customers/
- https://techtarget.com/searchsecurity/news/366552399/Microsoft-AI-researchers-mistakenly-expose-38-TB-of-data
- https://securitybrief.com.au/story/squarex-warns-of-rising-browser-native-ransomware-threat
- https://en.wikipedia.org/wiki/2023_MOVEit_data_breach
- https://devops.com/squarex-researchers-expose-oauth-attack-on-chrome-extensions-days-before-major-breach/