When done right, DevOps brings several value-added benefits. From enhanced agility, faster time to market, and reduced costs to dynamic provisioning, serverless computing, and flexible pay-as-you-go plans. But all these gains can go for a toss in an instant if “security” is not your top priority.
So, if you leverage DevOps for better productivity & enhanced client satisfaction while ignoring security issues, you’ll end up carrying water uphill in a sieve! On the contrary, the ‘Sec’ in DevSecOps can be the Jarvis to your Iron Man – A dependable sidekick that provides consistent support in your efforts.
And to give you a headstart, this article offers a complete rundown of everything you need to know to implement a smart DevSecOps strategy.
What is DevSecOps?
Modern enterprises are leveraging the collaborative approach of DevOps to automate rapid & reliable product delivery.
But what about security?
How are they mitigating vulnerabilities in the software development lifecycle? DevSecOps is their Strategy!
The goal is to implement checks on the same scale as app development. This approach eliminates the possibility of a threat at a later stage which would otherwise call for reworking countless lines of code – a tedious, time-consuming, and labor-intensive task!
Enterprises adopt this strategy because:
- Security is built into the product; not treated as an afterthought
- It ensures transparent workflows & timely collaboration during the development
- It facilitates faster recovery in case a threat is detected
Why DevSecOps Should be Your Top Priority?
Any lapse in security measures can invite a major loss of revenue & reputation. The risks of relaxed patches are immediate and expensive.
An American multinational hospitality brand suffered a loss of $123 million in litigation-related expenses. It was also imposed with hefty fines due to a safety breach that exposed the data of their 50 million guests. No kidding, but you see their brand reputation took a huge blow!The business case for DevSecOps is crystal clear. It drives performance, profits, and prominence!
Benefits of DevSecOps
- Automates securing of code to reduce vulnerabilities in apps while enabling predictable processes.
- Issues can be identified & resolved much faster in the early stages of the SDLC (Software Development Life Cycle)
- Helps ensure and maintain compliance in the CICD pipeline from day one
- Offers more agility and pace to the assigned teams
- Enhances trust and transparency between teams right from the start
- Increases the delivery rate and reduces costs
- Facilitates consistent security with automation tools for testing and reporting
- Creates an immutable environment that takes up lesser hands-on time for account management, event monitoring, assessing vulnerability, code security & deploying checks
- Enables security professionals to focus their efforts and attention on remediating threats and eliminating the risk
Key Components of DevSecOps Strategy
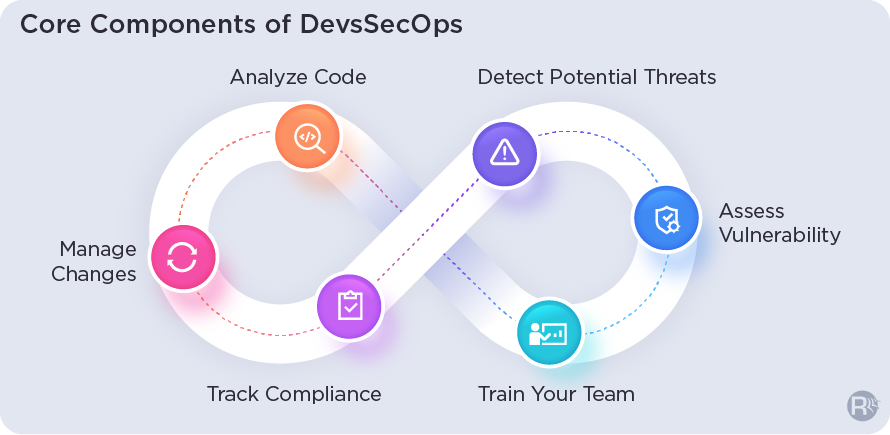
Enterprises need to adopt a cultural & technical mindset when leveraging this strategy to address their real-time security issues. A practical one entails six key components.
1. Analyze Code
Identify vulnerabilities on time with the delivery of code in small, manageable chunks.
2. Manage Changes
Submit changes that can accelerate development speed and efficiency. Also, determine if the outcome of change is favorable or not.
3. Track Compliance
Ensure compliance with all applicable regulations including Payment Card Industry Digital Security Standard (PCI DSS) & General Data Protection Regulation (GDPR) and always be prepared for regulatory audits.
4. Detect Potential Threats
Every code update accompanies impending threats. It is vital to uncover these threats at the earliest and respond promptly.
5. Assess Vulnerability
Systematically review all weaknesses that can leave the system vulnerable. Define and delegate security levels to known weak points and recommend corrective action as and when needed.
6. Train Your Team
Involve your development and IT-ops teams in security-related training and equip them with the standard operating guidelines for set workflows.
Rishabh with its end-to-end DevSecOps consulting services focus specializes in assessment, implementation, and support for client initiatives spanning from simple to complex IT projects. With our consultative solution focus, we enable clients to secure product development with DevSecOps capabilities. Our tailored platforms and custom frameworks help with integrating security into DevOps while building automation, testing, deploying & monitoring the production environment.
Common Pitfalls of DevSecOps & Best Practices to Overcome Them
A DevOps model typically involves cross-team collaboration. This brings in different workflows, specifications and approaches around planning, coding, deploying, testing, integration, infrastructure management and more.
Additionally, there is continuous monitoring and automation across the process chain. All of this results in fast-paced development cycles, accelerated release time and concise feedback loops. This dynamic environment can create gaps between the DevOps and security teams.
DevSecOps Challenges
1. Inability to Test Code at the Pace a DevOps Environment Demands
The short timelines of the DevOps team can surpass the pace of security teams who need to perform code analysis, assess vulnerability and check configurations among other routine tasks. These inconsistencies may result in misconfigurations, ineffective code, and hardcoded issues due to improper checks. Ultimately all this slows down the software development cycle.
2. Internal Friction
Cultural resistance often crops up a key issue of concern when addressing challenges in DevOps. This is often supported by the argument that special checks derail the development cycle. But in reality, addressing security concerns early on takes up much less time than taking a reactive approach at the last minute.
3. Cloud Deployments
The DevOps team essentially relies on open-source tools and cloud deployments to tackle security and server issues. Such a fast-paced environment often gives rise to erroneous configurations, compliance issues, and compromises mission-critical information leading to breaches.
4. Containerization
Container tools boost productivity but the same tools can also invite security issues. While containerizations bring you the agility to run on any cloud platform independently, it gives rise to challenges if you are not using proper controls. Container tools share the operating system, and they are rarely checked for vulnerabilities.
5. Access Control
DevOps is a hyper-connected, dynamic and collaborative approach. Teams keep sharing credentials, APIs, SSH keys, tokens and other critical information. This data is passed across containers, cloud instances, apps, and open-source platforms.
These platforms are susceptible to attacks and so, the assets passing through them are also subject to threats. This can give intruders control over data and systems, inviting serious issues.
We’ve seen the challenges at scale. Now let’s explore the best strategies to address these challenges.
DevOps Security Best Practices
Here are 9 proven practices that can help you achieve security without compromising on agility.
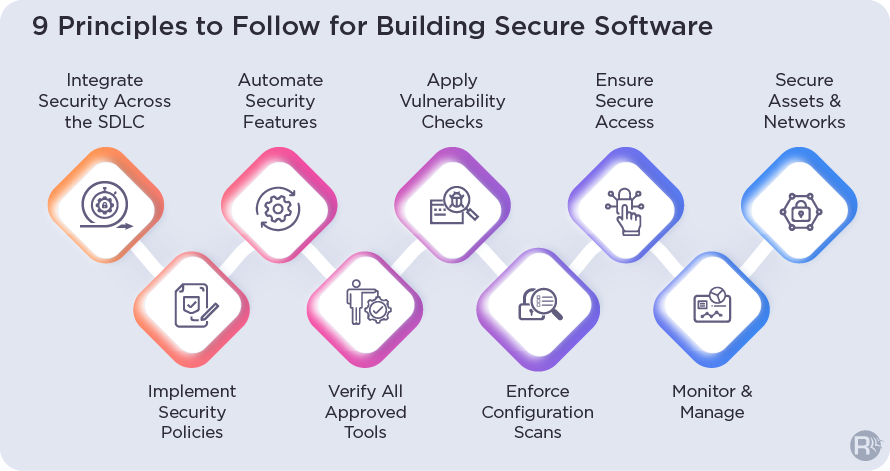
1. Integrate Security Across SDLC
Implementing the DevSecOps model brings you the advantage of cybersecurity measures such as firewalls, identify access management, code review, and vulnerability management. This governance ensures a secure DevOps environment that ensures seamless and speedy delivery.
2. Implement Security Policies
Strict enforcement of policies is the key to ensuring secure DevOps. Roll out transparent cybersecurity regulations that are comprehensive and easy to execute for the teams. This will help them plan their workflows in line with the defined guidelines.
3. Automate Security Features
Automating security tools minimizes the risk of errors occurring due to repeated instances inviting downtime issues. Scaling features also helps detect vulnerable code and impending threats or other issues within the environment. It also disrupts cultural resistance and reinforces the implementation of DevOps security practices in the process chain.
4. Verify All Approved Tools
It is equally crucial to consistently verify all the approved tools, accounts, and devices spotted during the discovery when you detect and map issues. Be sure to highlight them under security measures that are aligned with your internal guidelines.
5. Apply Vulnerability Checks
Ensure you have a stringent vulnerability assessment and management process in place before the product reaches the production environment. Conduct all vulnerability scans in advance and in tandem with the development and integration levels. Run a set of tools and tests in the production when the product enters the environment to resolve all patching-related issues.
6. Enforce Configuration Scans
Misconfigurations are a serious issue that can hit your workflow. Maintain and monitor configuration scans across individual builds and servers for all cloud assets consistently. All issues must be addressed in line with the best industry practices.
7. Ensure Secure Access
Be sure to delete all the credentials that are embedded in files, code, service accounts & cloud platforms. Store them safely at a centralized location where they can be accessed using privileged password management solutions. Leveraging such API calls ensures total control over embedded keys, code, and scripts.
8. Monitor & Manage
Secure all privileged account details and remove administrator rights on the user side to ensure a seamless workflow. Simultaneously, keep an eye on the privileged sessions to ensure legitimacy and adherence to compliance regulations. Restrict access only to production systems while giving internal teams the authority to design, deploy, and resolve development issues. Leverage access management resources to track and audit access and credentials.
9. Secure Assets & Networks
Classify networks and combine assets including resource servers and apps to restrict the line of sight for intruders. Create individual groups that function as logical units. Activate a secure jump server enabled with robust authorization features to ensure access from a reliable zone. Further segment all access-based context for different apps, data and end-users.
Clear as water, security creates a solid foundation for a full-fledged DevOps implementation. With issues addressed, it is undeniably a game-changer that efficiently caters to fast-changing business needs.
Core DevOps Security Tools
Implementing DevSecOps process flow involves code testing and assessment of risks for which you need specialized tools.
The core tools that are used to facilitate the different aspects of DevSecOps implementation are:
- Visualization: Grafana & Kibana are designed to help detect, develop and share security data with operations
- Automation: StackStorm helps ensure scripted remediation when threats are spotted
- Tracking: MozDef, OSSEC, GRR & Mirador are a few tools that help in detecting anomalies
- Testing: Chef Inspec, Spyk, Lynis, Hakiri, Gauntlt, and Infer are used for testing
- Alerting: Alerta, 411 & Elastalert trigger alerts with instant notifications upon detecting defects that need remediation
- Threat Intelligence: Critical Stack, Open TPX and Passive Total efficiently capture and collect threat intelligence
- Attack Modeling: CAPEC, CAIRIS, Infection Monkey & Randori help operationalize defenses
DevSecOps Use Cases
Automated Testing
- Identifying potential issues before the testing kickstarts
- Automated management of security issues detected in real-time during the testing process
- Resolution of issues identified during development, deployment & testing
- Auditing & documentation of issues
- Monitoring and management of testing & quality checks
- Enhanced development awareness & improved collaboration
- Consistent configurations across all environments
- Simulated testing driven by artificial intelligence
Process Optimization
- Adjusting change management procedures for moving apps from Development to Testing to Production environments based on historical data
- Smart and effective management of code freeze & un-freeze
- Optimizing the SDLC based on data obtained from the delivery history of prior projects
- Prioritizing response and assigning alerts to the concerned teams based on past data
- Automated compliance checks across apps, integrations, and environments
Automating CI/CD Workflows
- Collating data on the success or failure of the build and assigning automated alerts
- Orchestrating complicated pipelines
- Automated segmentation & root cause analysis of deployment data
- Flagging potential problem areas for future builds using predictive analytics
- Assigning bug fixes and management of issues to the right people, based on design and deploy data from past projects
- Embedding security testing across the DevOps lifecycle
- Optimizing and implementing “Infrastructure as code” culture
Enhanced Collaboration
- Proactively identifying the potential to facilitate continuous feedback loops
- Making recommendations to address security issues promptly
- Enabling real-time collaboration between the development, security & operations teams
- Automated posting of problems and tagging different teams in collaboration tools
- Analyzing data streams generated from various heterogeneous tools and systems to establish correlations and achieve a holistic view of new deployments, production problems, and the app’s health
Rishabh’s DevSecOps Consulting Approach
As a trusted and top-rated DevOps service and solutions provider, we leverage an industry-leading technology stack to achieve speedy deployment without compromising on software quality and security.
Our full-scale service focus comprises industry-specific consultations, custom implementation, automation, and management driven by proven methodologies that deliver best-in-class software, faster.
Our proficient team is backed by unmatched hands-on experience across tools like Kubernetes, Jenkins, Docker and more to enable secure and seamless implementations.
We will help you embed DevOps security across every stage of the delivery pipeline while ensuring all the tools & technologies are aligned with your regulatory requirements.











 30 Min
30 Min


